Deep Malware Analysis - Architecture independent Malware Similarity Analysis with Joe Sandbox Class 3.0

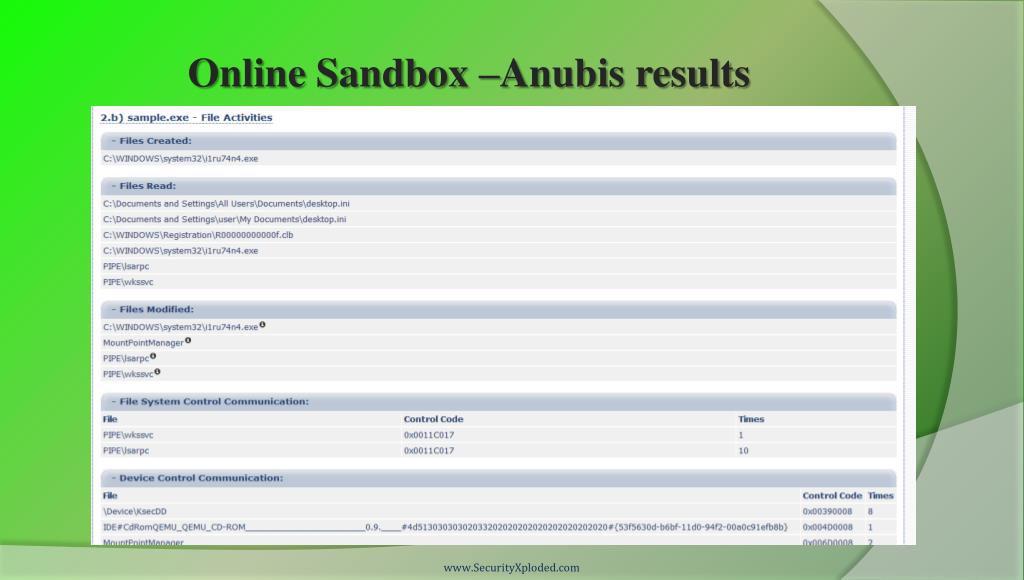
List of system activities from Anubis sandbox A number of input samples... | Download Scientific Diagram

Outline Infections 1) r57 shell 2) rogue software What Can We Do? 1) Seccheck 2) Virus total 3) Sandbox Prevention 1) Personal Software. - ppt download

List of system activities from Anubis sandbox A number of input samples... | Download Scientific Diagram